Motivation
The proliferation of third-party libraries in modern software systems introduces significant security risks, as these libraries often execute with far more privileges than necessary. Traditional privilege models, which operate at the program level, fail to provide sufficient granularity, leaving applications vulnerable to exploitation through sensitive operations such as file access, command execution, and network communication. This challenge is further exacerbated in dynamic, heterogeneous environments like those enabled by 5G, where applications must interact across scales while maintaining strict security guarantees.
Project Objectives
Our project aimed to address these challenges by redefining privilege management and enabling secure, scalable applications in zero-trust environments. Moving beyond the static assumptions of the initial proposal, we developed tools like Lucien, which learns and enforces fine-grained, context-aware library privileges at runtime. Additionally, we created Atlas, a system for securely offloading resource-intensive computations from IoT devices, demonstrating how tailored solutions could provide both security and efficiency across diverse use cases.
Key Contributions
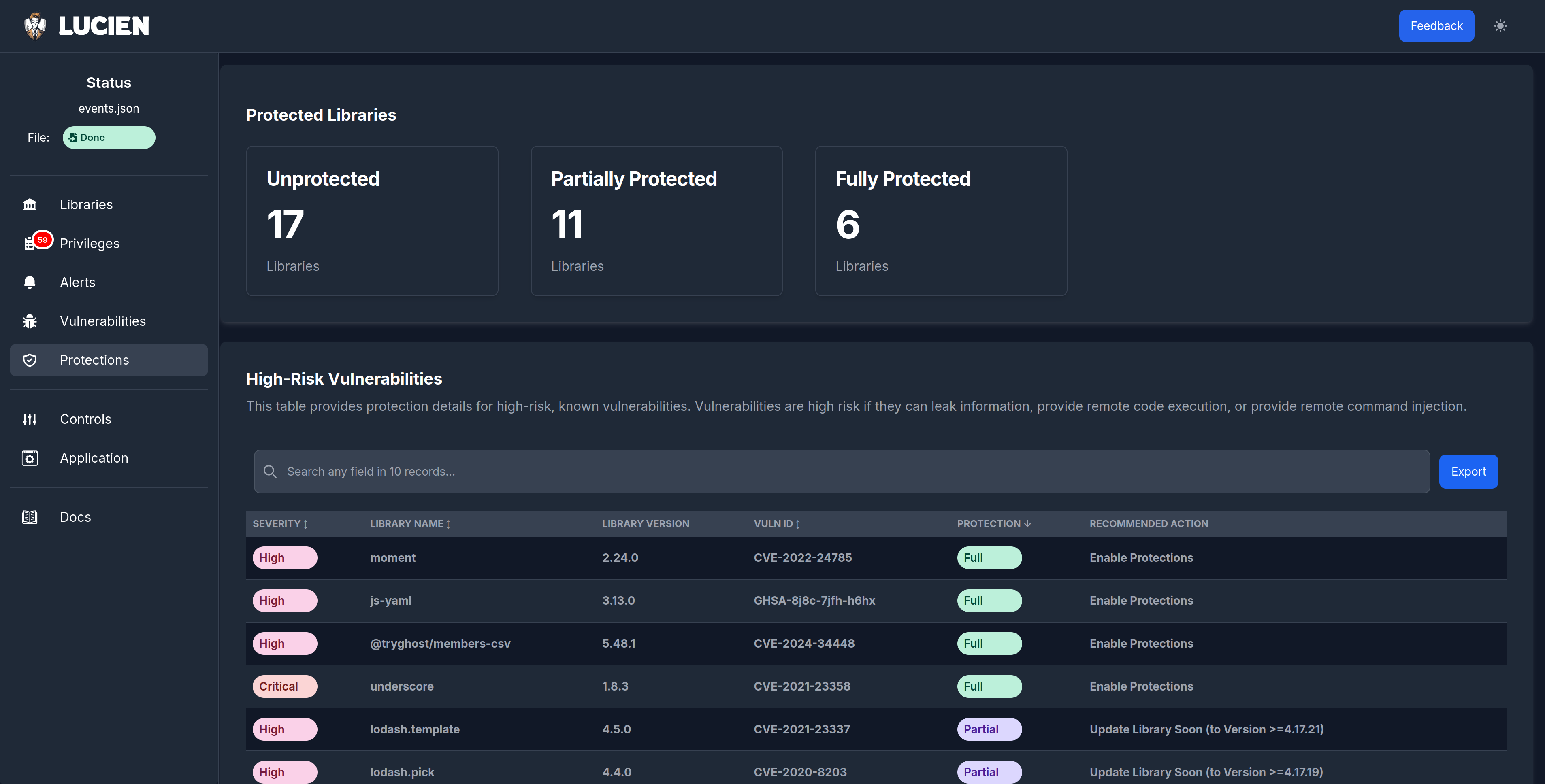
Lucien introduced a novel privilege model that tracks and enforces operations at the library level, combining call-specific actions with context-awareness through library traces. This approach enables precise restrictions without disrupting application functionality and significantly mitigates risks from vulnerabilities, including code injection, path traversal, and command injection. Atlas complemented this by securely offloading computation, leveraging Intel SGX enclaves to ensure data integrity even in zero-trust scenarios. Together, these tools provide a foundation for scalable, secure application design in highly heterogeneous environments.
Impact and Future Directions
The project demonstrated how fine-grained privilege models and secure computation offloading can transform application security and performance. By achieving near-zero runtime overhead and compatibility with existing software ecosystems, our tools reduce barriers to adoption while enhancing security in critical systems. For Lucien, In-Q-Tel Emerge awarded Aarno Labs commercialization funding, which enabled us to start a spin-off to mature and commercialize the fine-grained privilege technologies. Require and Aarno Labs have extended the base research to support multiple languages and environments and developed SASS and dashboard infrastructure for our customers. We have also published multiple academic papers detailing the research, and all core analysis implementation is open-source.
Papers
- Mir: Automated Quantifiable Privilege Reduction Against Dynamic Library Compromise in JavaScript. arXiv, 2021
- Preventing Dynamic Library Compromise on Node.js via RWX-Based Privilege Reduction. CCS, 2021
- Practically Correct, Just-in-Time Shell Script Parallelization. OSDI, 2022
- BinWrap: Hybrid Protection Against Native Node.js Add-ons. Asia CCS, 2023
Blog Posts
Funding Source
Sub to MIT CSAIL for DARPA: Open, Programmable, Secure 5G (OPS-5G)
Program Dates
Start: September, 2020
End: September, 2024

