The DroidSafe project developed effective program analysis techniques and tools to uncover malicious code in Android mobile applications. The system's core is a static information flow analysis that reports the context under which sensitive information is used. For example, "Application A has the potential to send location information to network address 128.6.21.6 on 'Button B’ press". The DroidSafe project invested significant time in developing a comprehensive semantic model of Android runtime behaviors alongside the analysis to achieve acceptable precision, accuracy, and scalability for real-world Android applications. The analysis was delivered to an operator in the context of an IDE plugin that displays intuitive information on the sensitive information sources, flows, and sinks of the untrusted application.
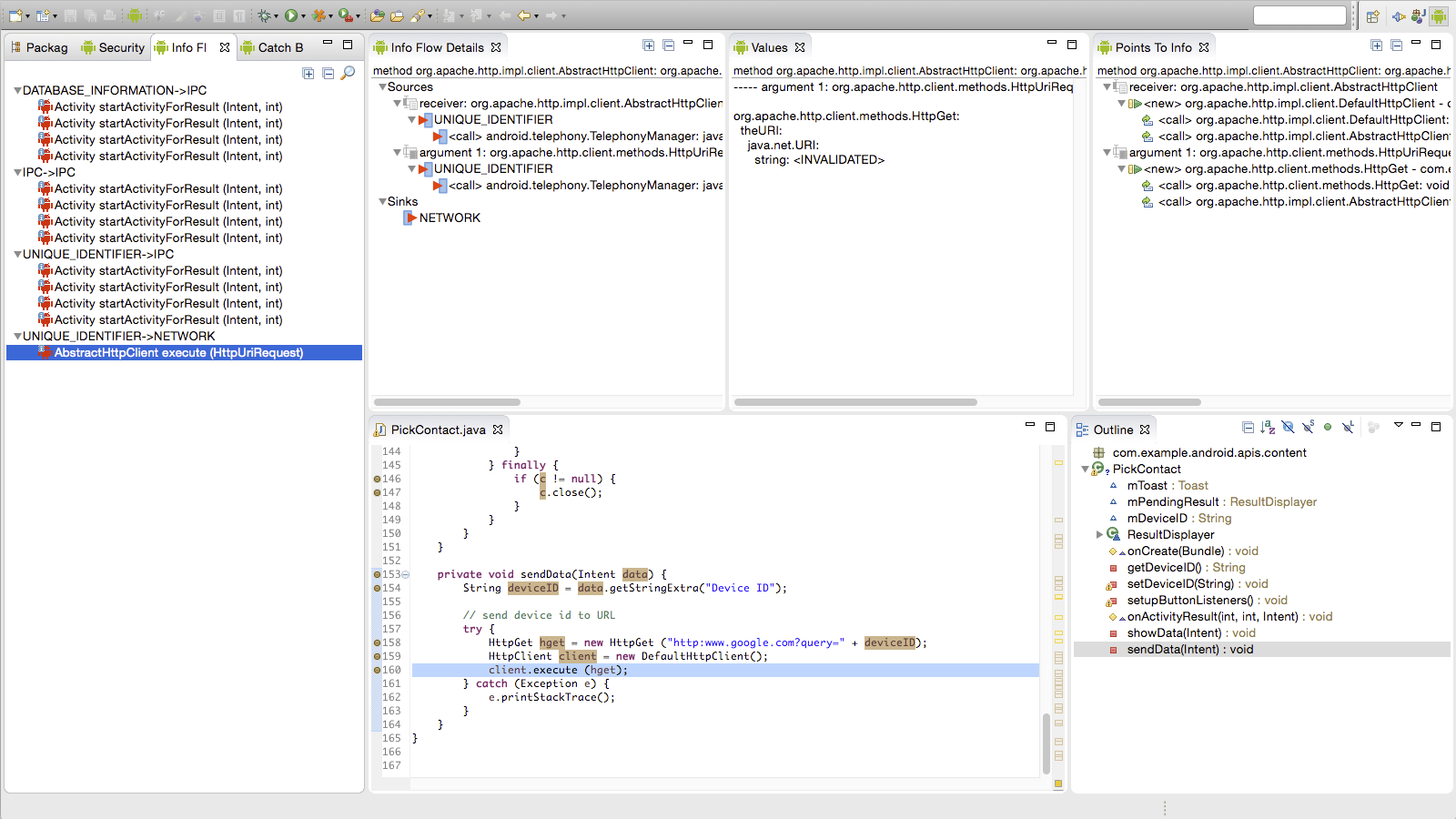
The combined system was demonstrated to be the most precise and accurate information flow analysis for Android applications. The analysis results can be used to check applications for security policy violations automatically, and the results can help a human analyst inspect sensitive behaviors of an app, increasing the accuracy and throughput of application vetting. For each of the last six DARPA APAC engagements, the DroidSafe team was unsurpassed in malware diagnosis accuracy with the least amount of human analysis time.
The information flow analysis system was the main focus of the DARPA APAC transition. The system was transitioned to Raytheon BBN and incorporated into their Artemis application security system. The entire analysis system and Eclipse plugin are open-source.
Artifacts and Links
- Github: Source code for static analysis system and Android model
- Documentation: Documentation for the analysis system
Papers
- Information Flow Analysis of Android Applications in DroidSafe. NDSS, 2015
- Covert Communication in Mobile Applications. ASE, 2015
- DroidSafe: Final Report. Aarno Labs Technical Report, 2019
Funding Source
Sub to MIT CSAIL for DARPA: Automated Program Analysis for Cybersecurity (APAC)
Program Dates
Start: May, 2015
End: January, 2017

